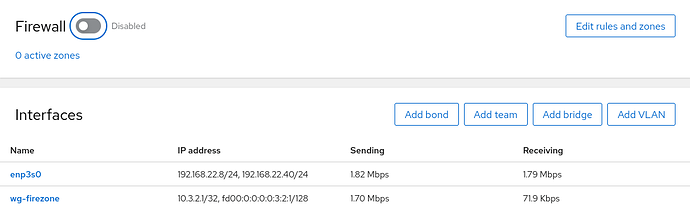
Hello
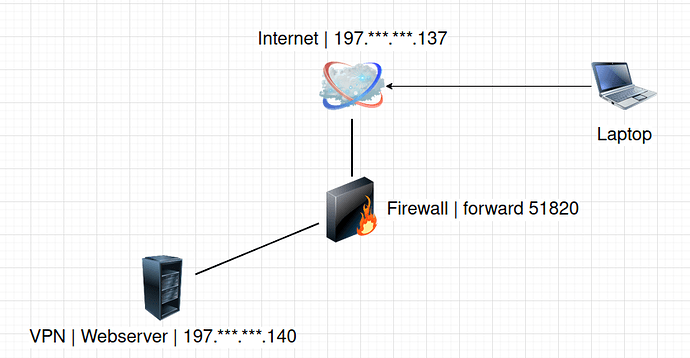
The config of firezone, endpoint = 197..
The problem is I disconnected from internet when I connect to wireguard.
jamil
July 1, 2022, 4:17am
2
Hi @elhanan – we’ll need more debugging information:
@jamil thanks for replying
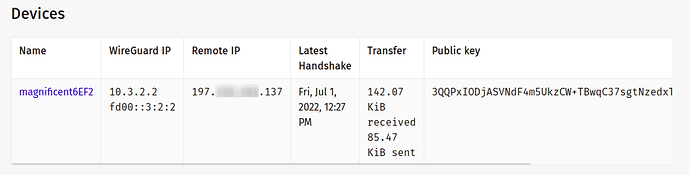
Are handshakes occurring?
Yes
This is from my phone connected using a hotspot on an internal network.
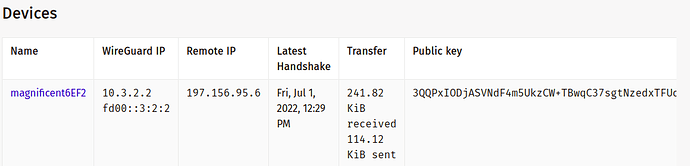
This is from my phone connected using mobile data
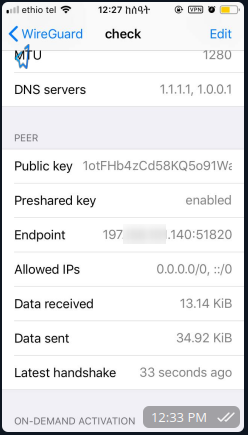
Mobile Screenshot:
Is your server firewall blocking forwarded packets? Troubleshoot | Docs Firezone
I think so, when I disable the firewall I can connect to the internet from my phone, But, I have allowed port 51820 in a public zone, Do I need to do additional settings on the firewall?
gbe0
July 1, 2022, 11:00am
4
Hi,
Since the handshakes are working, it sounds like the problem is a rule blocking forwarded traffic.
Can you provide the output of this with the firewall enabled (in the broken state):
nft list ruleset
1 Like
@gbe0 yeah, here is the output from nft list ruleset
table inet firezone {
chain forward {
type filter hook forward priority filter; policy accept;
}
chain postrouting {
type nat hook postrouting priority srcnat; policy accept;
oifname "enp3s0" masquerade persistent
}
}
table inet firewalld {
chain mangle_PREROUTING {
type filter hook prerouting priority mangle + 10; policy accept;
jump mangle_PREROUTING_ZONES
}
chain mangle_PREROUTING_POLICIES_pre {
jump mangle_PRE_policy_allow-host-ipv6
}
chain mangle_PREROUTING_ZONES {
iifname "enp3s0" goto mangle_PRE_FedoraServer
goto mangle_PRE_FedoraServer
}
chain mangle_PREROUTING_POLICIES_post {
}
chain nat_PREROUTING {
type nat hook prerouting priority dstnat + 10; policy accept;
jump nat_PREROUTING_ZONES
}
chain nat_PREROUTING_POLICIES_pre {
jump nat_PRE_policy_allow-host-ipv6
}
chain nat_PREROUTING_ZONES {
iifname "enp3s0" goto nat_PRE_FedoraServer
goto nat_PRE_FedoraServer
}
chain nat_PREROUTING_POLICIES_post {
}
chain nat_POSTROUTING {
type nat hook postrouting priority srcnat + 10; policy accept;
jump nat_POSTROUTING_ZONES
}
chain nat_POSTROUTING_POLICIES_pre {
}
chain nat_POSTROUTING_ZONES {
oifname "enp3s0" goto nat_POST_FedoraServer
goto nat_POST_FedoraServer
}
chain nat_POSTROUTING_POLICIES_post {
}
chain filter_PREROUTING {
type filter hook prerouting priority filter + 10; policy accept;
icmpv6 type { nd-router-advert, nd-neighbor-solicit } accept
meta nfproto ipv6 fib saddr . mark . iif oif missing drop
}
chain filter_INPUT {
type filter hook input priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
jump filter_INPUT_ZONES
ct state invalid drop
reject with icmpx admin-prohibited
}
chain filter_FORWARD {
type filter hook forward priority filter + 10; policy accept;
ct state { established, related } accept
ct status dnat accept
iifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 addr-unreachable
jump filter_FORWARD_ZONES
ct state invalid drop
reject with icmpx admin-prohibited
}
chain filter_OUTPUT {
type filter hook output priority filter + 10; policy accept;
ct state { established, related } accept
oifname "lo" accept
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 addr-unreachable
jump filter_OUTPUT_POLICIES_pre
jump filter_OUTPUT_POLICIES_post
}
chain filter_INPUT_POLICIES_pre {
jump filter_IN_policy_allow-host-ipv6
}
chain filter_INPUT_ZONES {
iifname "enp3s0" goto filter_IN_FedoraServer
goto filter_IN_FedoraServer
}
chain filter_INPUT_POLICIES_post {
}
chain filter_FORWARD_POLICIES_pre {
}
chain filter_FORWARD_ZONES {
iifname "enp3s0" goto filter_FWD_FedoraServer
goto filter_FWD_FedoraServer
}
chain filter_FORWARD_POLICIES_post {
}
chain filter_OUTPUT_POLICIES_pre {
}
chain filter_OUTPUT_POLICIES_post {
}
chain filter_IN_FedoraServer {
jump filter_INPUT_POLICIES_pre
jump filter_IN_FedoraServer_pre
jump filter_IN_FedoraServer_log
jump filter_IN_FedoraServer_deny
jump filter_IN_FedoraServer_allow
jump filter_IN_FedoraServer_post
jump filter_INPUT_POLICIES_post
meta l4proto { icmp, ipv6-icmp } accept
reject with icmpx admin-prohibited
}
chain filter_IN_FedoraServer_pre {
}
chain filter_IN_FedoraServer_log {
}
chain filter_IN_FedoraServer_deny {
}
chain filter_IN_FedoraServer_allow {
tcp dport 22 ct state { new, untracked } accept
ip6 daddr fe80::/64 udp dport 546 ct state { new, untracked } accept
tcp dport 443 ct state { new, untracked } accept
tcp dport 80 ct state { new, untracked } accept
tcp dport 9090 ct state { new, untracked } accept
udp dport 51820 ct state { new, untracked } accept
tcp dport 53 ct state { new, untracked } accept
udp dport 53 ct state { new, untracked } accept
tcp dport 3000 ct state { new, untracked } accept
tcp dport 3001 ct state { new, untracked } accept
}
chain filter_IN_FedoraServer_post {
}
chain nat_POST_FedoraServer {
jump nat_POSTROUTING_POLICIES_pre
jump nat_POST_FedoraServer_pre
jump nat_POST_FedoraServer_log
jump nat_POST_FedoraServer_deny
jump nat_POST_FedoraServer_allow
jump nat_POST_FedoraServer_post
jump nat_POSTROUTING_POLICIES_post
}
chain nat_POST_FedoraServer_pre {
}
chain nat_POST_FedoraServer_log {
}
chain nat_POST_FedoraServer_deny {
}
chain nat_POST_FedoraServer_allow {
}
chain nat_POST_FedoraServer_post {
}
chain filter_FWD_FedoraServer {
jump filter_FORWARD_POLICIES_pre
jump filter_FWD_FedoraServer_pre
jump filter_FWD_FedoraServer_log
jump filter_FWD_FedoraServer_deny
jump filter_FWD_FedoraServer_allow
jump filter_FWD_FedoraServer_post
jump filter_FORWARD_POLICIES_post
reject with icmpx admin-prohibited
}
chain filter_FWD_FedoraServer_pre {
}
chain filter_FWD_FedoraServer_log {
}
chain filter_FWD_FedoraServer_deny {
}
chain filter_FWD_FedoraServer_allow {
}
chain filter_FWD_FedoraServer_post {
}
chain nat_PRE_FedoraServer {
jump nat_PREROUTING_POLICIES_pre
jump nat_PRE_FedoraServer_pre
jump nat_PRE_FedoraServer_log
jump nat_PRE_FedoraServer_deny
jump nat_PRE_FedoraServer_allow
jump nat_PRE_FedoraServer_post
jump nat_PREROUTING_POLICIES_post
}
chain nat_PRE_FedoraServer_pre {
}
chain nat_PRE_FedoraServer_log {
}
chain nat_PRE_FedoraServer_deny {
}
chain nat_PRE_FedoraServer_allow {
}
chain nat_PRE_FedoraServer_post {
}
chain mangle_PRE_FedoraServer {
jump mangle_PREROUTING_POLICIES_pre
jump mangle_PRE_FedoraServer_pre
jump mangle_PRE_FedoraServer_log
jump mangle_PRE_FedoraServer_deny
jump mangle_PRE_FedoraServer_allow
jump mangle_PRE_FedoraServer_post
jump mangle_PREROUTING_POLICIES_post
}
chain mangle_PRE_FedoraServer_pre {
}
chain mangle_PRE_FedoraServer_log {
}
chain mangle_PRE_FedoraServer_deny {
}
chain mangle_PRE_FedoraServer_allow {
}
chain mangle_PRE_FedoraServer_post {
}
chain filter_IN_policy_allow-host-ipv6 {
jump filter_IN_policy_allow-host-ipv6_pre
jump filter_IN_policy_allow-host-ipv6_log
jump filter_IN_policy_allow-host-ipv6_deny
jump filter_IN_policy_allow-host-ipv6_allow
jump filter_IN_policy_allow-host-ipv6_post
}
chain filter_IN_policy_allow-host-ipv6_pre {
}
chain filter_IN_policy_allow-host-ipv6_log {
}
chain filter_IN_policy_allow-host-ipv6_deny {
}
chain filter_IN_policy_allow-host-ipv6_allow {
icmpv6 type nd-neighbor-advert accept
icmpv6 type nd-neighbor-solicit accept
icmpv6 type nd-router-advert accept
icmpv6 type nd-redirect accept
}
chain filter_IN_policy_allow-host-ipv6_post {
}
chain nat_PRE_policy_allow-host-ipv6 {
jump nat_PRE_policy_allow-host-ipv6_pre
jump nat_PRE_policy_allow-host-ipv6_log
jump nat_PRE_policy_allow-host-ipv6_deny
jump nat_PRE_policy_allow-host-ipv6_allow
jump nat_PRE_policy_allow-host-ipv6_post
}
chain nat_PRE_policy_allow-host-ipv6_pre {
}
chain nat_PRE_policy_allow-host-ipv6_log {
}
chain nat_PRE_policy_allow-host-ipv6_deny {
}
chain nat_PRE_policy_allow-host-ipv6_allow {
}
chain nat_PRE_policy_allow-host-ipv6_post {
}
chain mangle_PRE_policy_allow-host-ipv6 {
jump mangle_PRE_policy_allow-host-ipv6_pre
jump mangle_PRE_policy_allow-host-ipv6_log
jump mangle_PRE_policy_allow-host-ipv6_deny
jump mangle_PRE_policy_allow-host-ipv6_allow
jump mangle_PRE_policy_allow-host-ipv6_post
}
chain mangle_PRE_policy_allow-host-ipv6_pre {
}
chain mangle_PRE_policy_allow-host-ipv6_log {
}
chain mangle_PRE_policy_allow-host-ipv6_deny {
}
chain mangle_PRE_policy_allow-host-ipv6_allow {
}
chain mangle_PRE_policy_allow-host-ipv6_post {
}
}
gbe0
July 1, 2022, 2:07pm
6
At a glance its because the chain filter_FORWARD rejects the traffic since there isn’t a match permitting the wireguard sourced traffic. You could change the reject rule to match traffic except into the wireguard interface which should fix it (maybe)?
1 Like
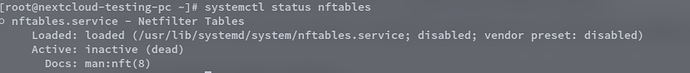
@gbe0 thanks for suggesting the solution, am not familiar with nftables but am trying to change the config. But one thing I noticed is nftables service is not running,
so how can its config affect wireguard connectivity? Thanks
gbe0
July 4, 2022, 12:02pm
8
If you check the contents of nftables.service it is simply a “One Shot” type of service which loads a set of nftables rules from a file. There can be various other tools that manage the firewall such as firewalld or ufw.
Based on the output of your rule set it looks like you are running firewalld which is adding the relevant rules.
1 Like
I added a new rule using thisnft insert rule inet firewalld filter_FORWARD udp dport 51820 accept and still no luck, did I miss somethin?
chain filter_FORWARD { # handle 18
type filter hook forward priority filter + 10; policy accept;
udp dport 51820 accept # handle 193
ct state { established, related } accept # handle 31
ct status dnat accept # handle 32
iifname "lo" accept # handle 33
ip6 daddr { ::/96, ::ffff:0.0.0.0/96, 2002::/24, 2002:a00::/24, 2002:7f00::/24, 2002:a9fe::/32, 2002:ac10::/28, 2002:c0a8::/32, 2002:e000::/19 } reject with icmpv6 addr-unreachable # handle 53
jump filter_FORWARD_ZONES # handle 36
ct state invalid drop # handle 38
reject with icmpx admin-prohibited # handle 39
}
@gbe0 now I figured it out, I added this to the filter_FORWARD chain and it worked now.
`nft insert rule inet firewalld filter_FORWARD iifname "wg-firezone" accept`
my only problem, for now, is making this rule permanent, am trying to read on that. Thank you for point out where the problem might be.
@jamil @gbe0 I solved this issue on my fedora server 36 using just this command:firewall-cmd --permanent --zone FedoraServer --add-forward
I suggest if this thing is added to firezone docs just as one of the issues might happen and troubleshoot on fedora. Thank you for this great tool and your support
1 Like